MSP
Achieve a fully operational zero trust-based security framework for networks and endpoints using the ColorTokens Xtended ZeroTrust™ Platform.
Zero trust provides optimal security for the modern enterprise
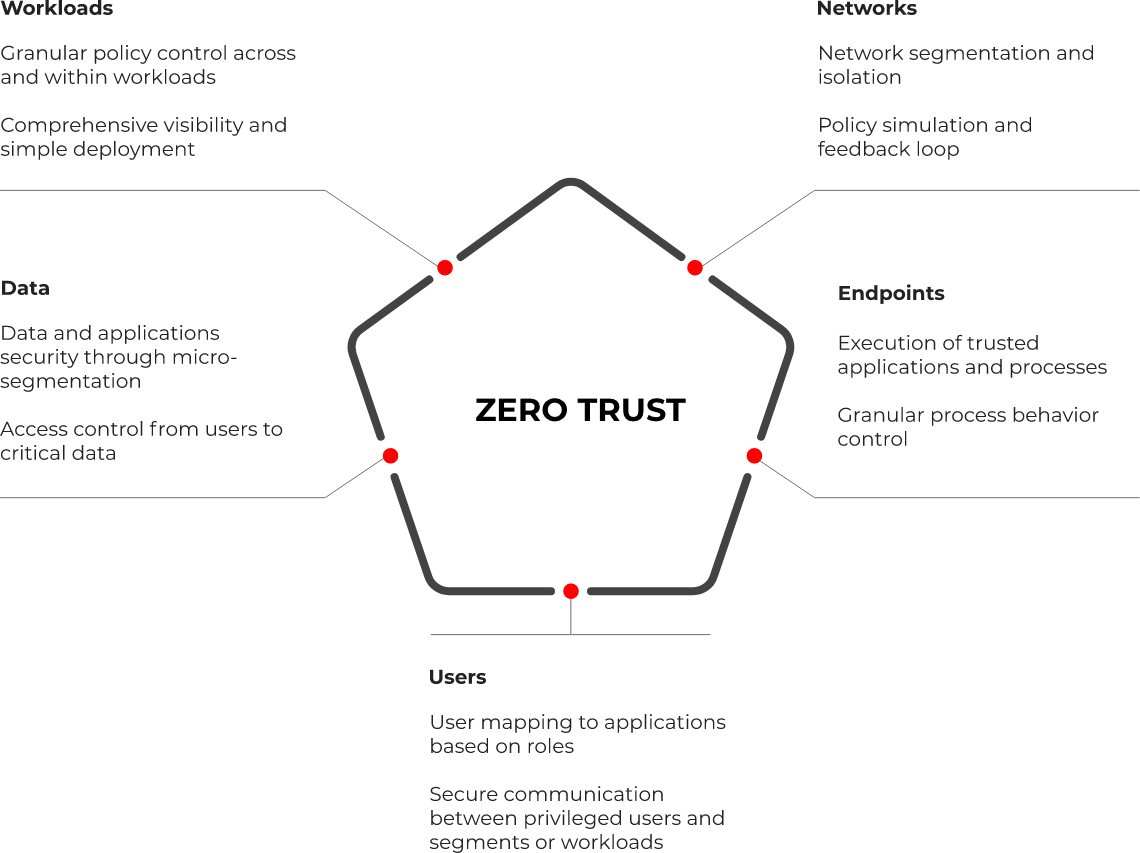
Why Zero Trust Adaption
Zero trust provides optimal security for the modern enterprise, which is increasingly cloud-based, perimeterless, and supports a remote workforce. The service is aligned with NIST’s Zero Trust Architecture (NIST Special Publication 800-207).
The Zero Trust Adoption service (ZTA) uses a proprietary framework to
deliver an outcome-driven solution and derive early business value from
zero trust implementation. The ZTA framework addresses the following
five dimensions of zero trust architecture
Trust nothing inside or outside your network and cloud infrastructure
Verify every access and every device that communicates and connects to your systems in the cloud and the data center
Minimize lateral movement. Prevent bad actors and anticipate breaches.

Installation on Workloads and Endpoints
The service provides rapid deployment of Xshield and Xprotect agents on workloads, servers, and endpoints.
Configuration to Suit the Infrastructure Architecture and Use CasesStreamline Compliance Audits
The service assesses the infrastructure architecture and configures the deployed products to ensure an optimized setup.
Zero Trust Design
Simple Solutions solution architects work very closely with IT teams to understand enterprise security requirements, priorities, concerns, network architecture, and existing policies. The solution architects then define micro-segmentation for workloads and servers. Security profiles are designed for endpoints, taking into consideration user profiles, authorized applications, and access
Implementation of Security Policies, Simulation, and Enforcement
Policies are designed to secure East-West and North-South traffic. Endpoint policies secure user compute devices from malware and any unauthorized process executions. Policies are simulated, observed for a period of time, and then enforced. This ensures minimal disruption to operations.


Product Subscription for Xshield and Xprotect
The service includes a subscription for the cloud-delivered products deployed.
Want to go zero trust?
Request a Call Back
Do not hesitate to contact us.
Adding {{itemName}} to cart
Added {{itemName}} to cart
Loading...




